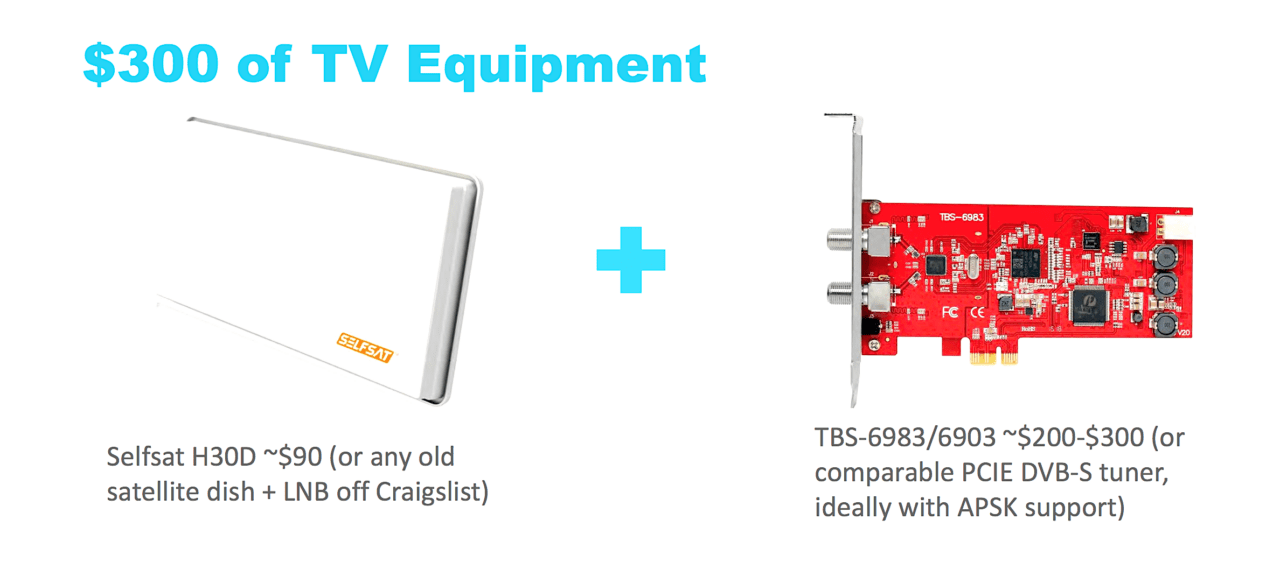
A research team used $300 worth of television equipment to demonstrate their ability to use “satellite eavesdropping,” to spy on in-flight passenger and flight crew Internet traffic.
Oxford PhD candidate and cybersecurity research James Pavur, along with a team of European experts, used about $300 in home television equipment and specialized software to enable “satellite eavesdropping” on in-flight passenger Internet data, as Pavur presented at Black Hat 2020 on August 5.
Pavur stressed that the tactics used by his team were nothing new, rather an update of methods manipulating satellite signals to expose consumer broadband Internet that were first published by researchers from Germany’s Ruhr-University Bochum in 2005, and then again by researchers separately at the 2009 and 2010 editions of Black Hat DC. Their only addition was a new software tool designed to enhance their ability to discover and decipher Internet traffic from satellite data.
The team’s setup included a Selfsat satellite dish with a TBS-6983/6903 PCIe card/Digital Video Broadcast-Satellite tuner computer card. Using the dish and tuner in combination with a program called EBS Pro that enables personal computer users to find and view satellite television feeds, Pavur’s team was able to analyze 4 terabytes of data on signals from 18 satellites in geostationary orbit.
Their equipment was compatible with Ku-band satellite signals, so the team focused on those. Instead of using EBS Pro to find satellite television signals, they instead captured Internet data packets used passengers on networks deployed across land, sea and air to enable access to the use of websites and other connected services that generate traffic across those same signals.
A key protocol, Generic Stream Encapsulation (GSE), was central to the team’s satellite signal manipulation. When attempting to use the combination of the PCIe card, satellite dish and EBS Pro alone, the majority of the feeds that they would capture were corrupted and missing fragments of Internet Protocol (IP) packets. This occurred because GSE uses an IP layer embedded inside of a generic stream that is further broken up into fragments before entering the satellite digital video broadcasting feeds that his team was hacking into.
“We found that GSE was particularly popular among enterprise customers, so people who had an entire satellite transponder for their network. Think, like maritime or aviation customers. But these customers also had much better equipment than we do,” Pavur said.
That led to their internal development of a software tool called GSE Extract, designed to “forensically reconstruct .PCAT files from recordings of GSE feeds,” Pavur said.
“It does this by taking some shortcuts. If we were designing a satellite modem, we would have to consider all of the edge cases and how a network operates or how a packet gets sent. But for GSE Extract, we can say, generally, we would expect the start of an IP packet to appear here, or we’d expect this fragment to belong to this payload. And, by making some of those assumptions, GSE Extract is able to help us figure out what to do with between 50 and 70 percent of the frames that were hitting our dish,” Pavur said.
Over the course of two years, they have been able to routinely see passenger and crew satellite Internet traffic on cargo and maritime ships. The researchers were able to get so detailed that during a recent exercise, they were able to capture a passenger’s use of a mobile phone email application while in-flight to confirm their receipt of a negative COVID-19 test.
“This is a JPEG file that we intercepted from an engineer aboard a maritime vessel who was dealing with a maintenance issue and sending pictures to his colleagues. You’ll see that we’re able to get like the start of the packet,” Pavur said.

The team described a vulnerable Chinese airline pilot’s electronic flight bag as the “loneliest EFB.”
Aviation was the newest industry used for the team’s research, which Pavur said was going to be their main focus for 2020. Once passenger traffic started to decline in March due to the COVID-19 pandemic, they started to notice that they could focus on flight crew devices, including data being transmitted by Electronic Flight Bag (EFB) tablets used by pilots.
Specifically, Pavur said he wanted to focus on the vulnerabilities that exist with modern commercial aircraft satellite Internet modems that have been demonstrated in the past by Ruben Santamarta, a cybersecurity researcher with independent security firm IOACTIVE. Santamarta posited his belief that the satellite terminals featured on aircraft used to separate passenger and pilot internet usage can be hacked.
“We found what I’m going to call the loneliest EFB,” Pavur said, referring to a Chinese airline pilot’s connected tablet whose Internet traffic they were able to monitor for several months.
“This specific Chinese airline had made a mistake in configuring their EFB, such that it wasn’t logging in correctly. And so all of the requests that it was sending were getting bounced off of this redirect page from the satellite modem and reaching us. And we could use that to not only fingerprint like how this API works and what sort of data is being sent from the airplane, but we could also identify other vessels that were using this same device,” Pavur said.
Pavur went on to describe in detail other real communications and text messages that they were able to view on passenger devices while in-flight. Overall, the setup used by their research team featured relatively inexpensive equipment, so theoretically a hacker with more advanced tools would probably be more accurate and find a fewer corrupt feeds or missed packet data.
Pavur said the flaws his team demonstrated in satellite eavesdropping affect “tens of thousands of satellite customers” and many of the satellite companies have known about his research since 2019. Their team is currently engaged in responsible disclosure communications with regulators researching the issue as well.
“When you connect to the Internet, there’s a whole web of different nodes and connections. It’s constantly changing. That’s routing your traffic and any one of those nodes could be a satellite link or a wireless tower or a wire tapped ethernet cable,” Pavur said. “So having the ability to encrypt your own traffic, having the right to encrypt your own traffic and having the knowledge to make that encryption as secure and robust as possible is I think critical to preventing this whole class of attack regardless of the domain, we consider it in.”