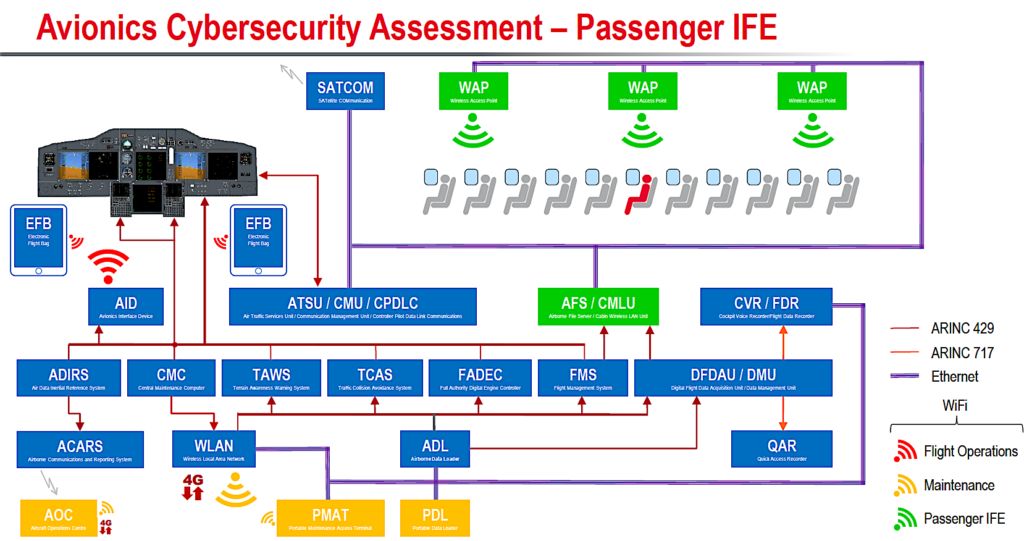
An overview of how connected aircraft systems work within modern commercial airplane networks. Photo: Curtiss Wright
SAN DIEGO – During the 2019 Global Connected Aircraft Summit, Avionics International discussed emerging cyber security threats to connected avionics systems becoming a reality as more high speed internet protocol (IP)-based connectivity is added to modern commercial airplanes with Paul Hart, Chief Technology Officer (CTO) of Curtiss Wright.
Check out our question and answer session with Hart below, along with diagrams he provided showing how hackers are looking to attack connected avionics systems architectures.
Avionics International: We would like to provide our audience with a deep understanding of how modern aircraft avionics systems function and how the addition of internet protocol-based connectivity pipes have exposed aircraft to possible cyber threats. Can you start with the basics of how hacking works within ground-based computer networks to prepare us for understanding how that works on airborne systems with aviation specific regulated network protocols?
Paul Hart: There are several classifications of malware that can infect a computing platform — viruses, worms, trojans, ransomware etc. — that work by attaching themselves to code within legitimate applications or the operating system and perform a disruptive function when the code is executed. Malware is primarily a concern in the IT world where, for example, an employee could unwittingly launch a malware application by clicking on a ‘you have won a prize’ icon that spreads through a network onto multiple computers in a building.
Fortunately the avionics architecture on an aircraft is inherently locked down from interactions with the outside world. The opportunities to introduce malware are very few, however the evolution of the connected aircraft has introduced certain risks if the security levels of wireless networks are breached.
AI: What would make a connected aircraft more vulnerable to these attacks?
PH: Let’s consider how a hacker could pull off an attack, and that really depends on the robustness of the wireless portals that connect to avionics systems. For example, many airlines issue Electronic Flight Bags (EFBs) to pilots in order to simplify the flight planning process, such as calculating take-off power and trim settings from the weight and balance electronic load sheet. Some EFBs connect via Wi-Fi to aircraft systems using an avionics interface device in order to retrieve parameters such as latitude or longitude position and outside air temperature for these calculations.
Should a tablet be lost or stolen and subsequently find itself in the hands of an experienced hacker it could be possible to breach a weak password and access the WiFi protected access key (WPA2). In turn a hacker could potentially bypass the digital signatures on the tablet, reload a different operating system and malicious applications that could cause a broadcast storm — essentially a denial of service hack — that could prevent flight crews operating EFBs or ground crews uploading new navigation databases.

An overview of how a “worm” cyber attack works. Photo: Curtiss Wright.
AI: How are the connected access points on aircraft protected from attacks today, and does Curtiss Wright provide any technology or guidance that could improve the security of those attack points?
PH: Satcom and VHF data links such as ACARS generally do not contain any secure information. For example, ACARS can be spoofed, but contains commercial data such as estimated flight arrival times and gate assignments. Avionics interface devices and wireless access points that provide the connectivity for the airline flight operations and maintenance staff and passengers respectively use layers of WPA2 security and encryption within the applications that connect the airborne server to the user.
AI: How can manufacturers actually go about evaluating and mitigating the risks of avionics that “connect” to the outside world, prior to actually achieving certification under the forthcoming EASA regulations?
PH: Methods to evaluate and mitigate cybersecurity risks across manufacturers, operators, maintainers, product suppliers (Avionics, EFBs) and service providers have been documented in Eurocae ED-201’s “Aeronautical Information System Security Framework Guidance.” This is a very comprehensive guide for identifying vulnerabilities to cyber attack and building the security environment to mitigate the threats. In turn, ED-201 references other Eurocae and RTCA standards that form the certification path adopted by EASA, FAA and other national airworthiness authorities.

All of the connected aircraft’s potential intrusion points. Photo: Curtiss Wright
AI: Internet protocol security standards can be built into embedded computing network layers. How would you see this occurring for an in-service aircraft, that has legacy systems and data bus architectures?
PH: In-service aircraft with legacy equipment will not have cybersecurity features to meet these requirements. However, there are upgrade paths available. For example, many avionics units require regular database updates which are commonly performed using a carry-on laptop or a portable data loader (PDL). These use the ARINC 615A point-to-point Ethernet protocol which has no security features beyond password access. Should an airline intend to connect the PDL port to a wireless network in order to upload such databases remotely as part of a zero-touch aircraft program, new security features would need to be implemented.
AI: What type of firewalls can protect connected avionics systems from possible intrusion?
PH: An inline firewall or secure gateway could be installed between the PDL port and the network switch or router that connects the PDL to the corresponding avionics unit. This could implement a virtual private network using IPSEC and MACSEC layers in order to authenticate the connection between the aircraft and the airline network, then create a session key to encrypt the data transfer while the systems are connected.